The subject of cybersecurity takes a focal place in organizations of all sizes. Most people tend to think that cybersecurity concerns IT professionals and C-suite executives. However, security should be a key concern for each employee in an organization. Hackers tend to use unsuspecting stakeholders as steppingstones to carrying out data breaches.
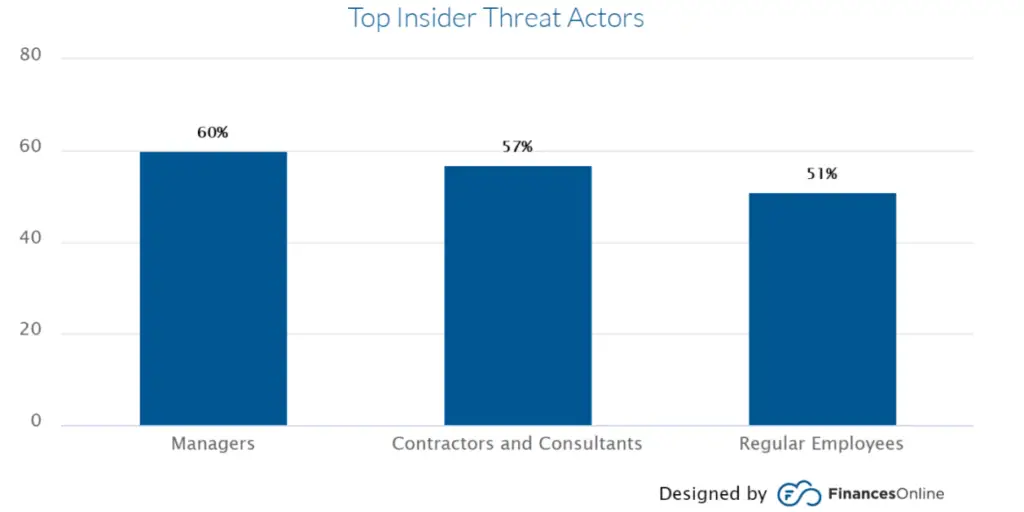
It is also important to note that these stakeholders play a role in insider threats. A Bitglass Insider Threat Report released in 2020 has identified managers, regular employees, contractors, and consultants as the most significant insider threat actors.
One of the best ways to deal with external and insider cybersecurity threats is having sound cybersecurity policies and conducting cybersecurity training. Cybersecurity policies for businesses provide a roadmap for cybersecurity. They also ensure compliance with cybersecurity regulations and guide stakeholders on best practices and response plans in case of a threat.
There are several cybersecurity policies that every business must consider. In this article, we examine nine must-have cybersecurity policies for businesses.
Acceptable Use Policy
Acceptable Use Policy (AUP) details explicit requirements that every computer and network resources user within a business must adhere to. Such resources include softcopy and hardcopy data, information assets, servers, and others.
The Acceptable Use Policies come into play to ensure that your business’s information resources and assets are only used for their intended purpose. All stakeholders must agree to this policy before they can be guaranteed access to the said assets. A network ID should only be granted to new employees who have read, understood, and signed the AUP.
Data Breach Response Policy

An Accenture report now reveals that 68% of business leaders are worried about the increasing cybersecurity threats. Cybercriminals are hitting organizations hard. Hackers have mastered the art of using the weakest links to their advantage. With so many cybersecurity threats such as phishing attacks, malware attacks, among others, it might just be a matter of time before the hackers come knocking. Today, data breaches are more likely than ever before.
SSL certificates have been at the forefront in the battle against data interceptions. They help in the encryption of data between website servers and web visitors. The cheap SSL certificate will be time-saving and cost-effective. The user can choose SSL Certificate according to their business requirement. For example, single-domain SSL will secure the domain, wildcard SSL will protect one multiple first-level subdomains under it. To secure multiple domains and subdomains at different levels, the Multi-Domain SSL is the right option.
With that in mind, you need to bolster your business security by having a sound response policy that addresses all possible threats. The response plan will make your business more equipped to deal with security threats. The response policy should address all the potential threats you are vulnerable to, your existing security tools and resources, and the resources you have to acquire to be super-equipped to address the threats.
Information Security Policy
This section of cybersecurity policies for businesses usually encompasses a series of high-level policies covering an array of security controls. The business issues the primary information security policy to guide all stakeholders through the safe use of technology assets, networks, and resources. Most businesses will issue the information security policy for signing alongside the acceptable use policy.
Stakeholders who sign the information security policy will be held accountable for the sensitivity of the organization’s information and IT resources. One of the best Information Security policies is the State of Illinois information security policy. You can use it for reference when creating yours.
Email/Communication Policy
![]()
The email/communication policy deals with how organizations communicate with other parties. This policy covers blogs, mail communications, and chat technologies. In addition, it stresses the need for encryption. Communication encryptions are vital because they keep hackers off the radar. One of the critical elements that must feature in this policy is the Secure Socket Layer.
The primary objective of the Email/communication policy is to enlighten all stakeholders about the acceptable and unacceptable use of organizational communication technology. For instance, employees should be made to only visit HTTPS websites.
Configuration Management Plan
Configuration is a less popular cybersecurity policy for businesses. It covers all the procedures undertaken to identify and document hardware and software components and all the associated settings. A configuration management plan is vital because it helps with disaster recovery. Ideally, it would not be easy to recover your system to a stable configuration if you do not have a clear picture of what or how the configuration was before the disaster.
Therefore, a configuration management plan should document new and old system components, hardware or programs, system hardening requirements, and patch management procedures.
Having security plugins
If you run a WordPress blog, it’s crucial to have effective cybersecurity policies in place to protect your website from cyber threats. One essential aspect of website security is the use of security plugins. WP Force SSL and WP Login LockDown are two of the best plugins available to enhance the security of your WordPress site. WP Force SSL allows you to obtain an SSL certificate for your website, which encrypts data transmission and ensures secure communication between the server and the browser. This certificate is essential for protecting your website from malicious attacks that attempt to steal sensitive information. WP Login LockDown, on the other hand, limits the number of login attempts from a single IP address, preventing hackers from gaining unauthorized access to your site. These plugins are easy to install and use, and they provide an added layer of security to your WordPress site, making them essential for any business that runs a website. By incorporating these plugins into your cybersecurity policies, you can help safeguard your website from cyber threats and ensure that your data and your customers’ data are protected at all times.
Safe Password Policies

Pretty much all stakeholders use passwords when logging into their work accounts. So it would help if you never hung it low for them. Passwords are one of the most critical cybersecurity players, which is why a sound password policy should set the bar high for your employees.
A password policy outlines the guidelines that every stakeholder must follow when creating their passwords. In addition, it passes them the wisdom of safe password practices. For instance, it must be mandatory for all stakeholders to develop and use unique passwords. Additionally, the policy should stipulate the minimum number of characters that each password should contain. Passwords should never be allowed to go below these thresholds.
You can also use the policy to encourage employees to use password management tools and warn them against poor password storage habits. Additionally, users should be encouraged not to use passwords they have already used elsewhere.
Disaster Preparedness and Recovery Policy
The disaster recovery policy aims to ensure the continuity of the business even after a data breach, data loss, or related security vulnerabilities. In addition, it helps to answer the question “what next after a data breach?”
Let us face it; a data breach is no longer a question of if but when. No one is absolutely immune to hackers. Despite the security tools and investments you might have made in data security, the relentless hackers will always find a way to navigate through your data. The disaster recovery plan is a business continuity plan that seeks to reduce the impact of a successful data breach. A sound disaster recovery plan should address elements such as frequent backups, effectiveness, and efficiency of the data recovery plan.
Remote Access Policy

With the increasing relevance of remote working due to the prevailing Covid-19 situation, remote working is almost inevitable for most businesses, and so is a remote access policy. Hackers have been shifting their attention to the least suspecting remote workforce. The remote access policy addresses such issues by outlining and defining acceptable practices for remote workers connecting to the businesses’ internal networks.
The policy may also carry addendums with regulations governing the use of Bring Your Own Devices (BYOD). This policy remains relevant to organizations that have dispatched a remote workforce.
You can also use a residential proxy network in creating and implementing effective cybersecurity policies as it can provide access control, content filtering, data leakage protection, auditing and compliance, and remote access to internal resources while maintaining a secure connection.
Access Control Policy
The Access Control Policy (ACP) is a privileged document that outlines the available privileges an employee has regarding a business’s data. The document should spell out the minimum amount of privileges a user should be granted to specific data, network, or other digital resources. The policy should also spell out the techniques used to access corporate networks and handling of unattended workstations. Proper guidelines should be laid to scrape off employees who leave your organization of access privileges.
Conclusion
The nine policies and guidelines mentioned above will help you build a robust cybersecurity defense strategy. It would help if you took your time to go through the attached templates for each policy to craft your perfect policies. Additionally, it would be best if you integrated all the policies to make them work in unison. I hope this article will help you create cybersecurity policies that will guide your business to success.

